In this week’s post, we will learn how to test for IDOR. IDOR stands for Insecure Direct Object Reference, and it refers to a situation when a user can successfully request access to a webpage, a data object, or a file that they should not have access to. We’ll discuss four different ways this vulnerability might appear, and then we’ll actually exploit this vulnerability in a test application using Chrome’s Developer Tools and Postman.
One easy way to look for IDOR is in a URL parameter. Let’s say you are an online banking customer for a really insecure bank. When you want to go to your account page, you login and you are taken to this URL: http://mybank/customer/27. Looking at this URL, you can tell that you are customer number 27. What would happen if you changed the URL to http://mybank/customer/28? If you are able to see customer 28’s data, then you have definitely found an instance of IDOR!
Another easy place to look is in a query parameter. Imagine that your name is John Smith, and you work for a company that conducts annual reviews for each of its employees. You can access your review by going to http://mycompany/reviews?employee=jsmith. You are very curious about whether your coworker, Amy Jones, has received a better review than you. You change the URL to http://mycompany/reviews?employee=ajones, and voila! You now have access to Amy’s review.
A third way to look for IDOR is by trying to get to a page that your user should not have access to. If your website has an admin page with a URL of http://mywebsite/admin, which is normally accessed by a menu item that is only visible when the user has admin privileges, see what happens if you log in as a non-admin user and then manually change the URL to point to the admin page. If you can get to the admin page, you have found another instance of IDOR.
Finally, it’s also possible to exploit an IDOR vulnerability to get files that a user shouldn’t have access to. Let’s say your site had a file called userlist.txt with the names and addresses of all your users. If you can log in as a non-admin user and navigate to http://mywebsite/files?file=userlist.txt, then your files are not secure.
Let’s take a look at IDOR in action, using Postman, Chrome Developer Tools, and an awesome website called the OWASP Juice Shop! The OWASP Juice Shop is an application created by Bjorn Kimminich to demonstrate the most prevalent security vulnerabilities. You can download it and run it locally by going to https://github.com/bkimminich/juice-shop, or you can access an instance of it by going to https://juice-shop.herokuapp.com. For this tutorial, we’ll use the heroku link. Once you navigated to the site on Chrome, create a login for yourself. Click the Login button in the top left, and then click the “Not yet a customer?” link. You can use any email address and password to register (don’t use any real ones!). Log in as your new user, and click on any of the juices on the Search page in order to add it to your shopping basket.
Before you take a look at your basket, open up the Chrome Developer Tools by clicking on the three dots in the top right corner of the browser, selecting “More Tools”, and then “Developer Tools”. A new window will open up on either the right or the bottom of your browser. In the navigation bar of the tools, you should see a “Network” option. Click on this. This network tool will display all of the network requests you are making in your browser.
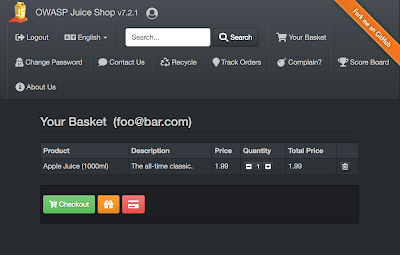
Click on the “Your Basket” link in the top right of the Juice Shop page. You will be taken to your shopping cart and you should see the juice that you added to the basket. Take a look in the Network section of the Developer Tools. The request that you are looking for is one that is named simply with a number, such as “6” or “7”. Click on this request, and you should see that the request URL is https://juice-shop.herokuapp.com/rest/basket/<whateverYourAccountIdIs>, and that the request type is a GET. Scrolling down a bit, you’ll see that in the Request Headers, the Authorization is set to Bearer and then there is a long string of letters and numbers. This is the auth token. Copy everything in the token, including the word “Bearer”.
Next, we’ll go to Postman. Click on the plus tab to create a new request. The request should already be set to GET by default. Enter https://juice-shop.herokuapp.com/rest/basket/<yourAccountId> into the URL. Now go to the Headers section, and underneath the Key section, type “Authorization”, and underneath the Value section, paste the string that you copied. Click to Send the request, and if things are set up correctly, you will be able to see the contents of your shopping basket in the response.
Now for the fun part! Change the account id in the URL to a different number, such as something between 1 and 5, and click Send. You will see the contents of someone else’s basket! Congratulations! You have just exploited an IDOR vulnerability!
Your blog helped to understand the concept of IDOR.
Nicely explained 🙂
Expecting more security test blogs
Thank You
I'm so glad you found it helpful, vjkumran!
This comment has been removed by a blog administrator.