Last week, we talked about three different ways to test for Cross-Site scripting. We looked at examples of manual XSS testing, and talked about how to use the code to formulate XSS attacks. Today we will look at the third way to test, which is to use automation. For today’s testing, we’ll be using Burp Suite, which is an oddly-named but very helpful tool, and is available for free (there is also a paid version with additional functionality). We’ll also be using the Juice Shop and Postman.
First, let’s take a look at the field we will be testing in the Juice Shop. Using the Chrome browser, navigate to the Juice Shop’s home page. You’ll see a search window at the top of the page. Open up the Chrome Developer Tools, by clicking on the three-dot menu in the upper right corner, then choosing “More Tools”, then “Developer Tools”. Once the dev tools are open, click on the Network tab.
Do a search for “apple” in the search field. You’ll get your search results on the web page, and you should see the network request in the developer tools. The request name will be “search?q=apple”. Click on this request. A window will open up with the full request URL, which should be https://juice-shop.herokuapp.com/rest/product/search?q=apple.
Next, open up Postman. Paste this URL into the URL window, and click the Send button. You should get a 200 response, and you should see your search results. Now we’ll set Postman to use a proxy. Click on the wrench icon in the top navigation bar and select “Settings”. Click on the Proxy tab, then turn the Global Proxy on. In the first section of the Proxy Server window, type 127.0.0.1, which is your local IP address. In the second section, type 8080, which is your local port. Postman is now set up to send requests to Burp Suite. You may need to do one more step here, which is to turn SSL verification off. In the Settings window, click on the General tab, and turn off the “SSL certificate verification” setting.
Once you have downloaded Burp Suite, start the application and click Next. Then click Start Burp. Now Burp Suite is ready to receive requests. Go back to Postman, and click Send on the search request that you sent earlier. It will appear that nothing happens; this is because the request has just been sent to Burp! Go to Burp, and you will see that the Proxy tab is now in an orange font. Click on the Proxy tab, and then click the Forward button. Your request is now being sent on to Postman, and if you return to Postman to check, you will see your request results. It’s a good idea to turn off the Global Proxy in Postman now, because if you forget, the next time you make a Postman request you’ll wonder why you aren’t getting results!
Return to Burp Suite, and click on the HTTP tab. (This is a sub-tab of the Proxy tab. If you don’t see the HTTP tab, make sure the Proxy tab is selected.) You should see your GET request listed here. Right-click on your request, and click “Send to Intruder”. You should see that the Intruder tab is now in an orange font.
Click on the Intruder tab. You can see that the attack target has already been set to the Juice Shop URL. Now click on the Positions sub-tab. This is where we choose which element of the request we want to replace. Burp Suite has guessed correctly that the element we’d like to replace in our testing is the search field value of “apple”, so we can leave this setting as-is. Now click on the Payloads sub-tab. Here is where we will try out a bunch of cross-site scripting payloads!
Enter in a bunch of XSS attacks into the Payload Options window, using the Add button. Here are some suggestions:
<script>alert(“XSS here!”)</script>
<script/src=data:,alert()>
<IMG SRC=javascript:alert(‘XSS’)>
<IMG SRC=JaVaScRiPt:alert(‘XSS’)>
<a onmouseover=”alert(document.cookie)”>xxs link</a>
You can find many more suggestions in this XSS Filter Bypass List. It’s worth noting that if you sign up for the paid version of Burp Suite, a whole list of XSS attacks will be available to use, saving you from having to type them in manually.
Let’s start our attack! Click the “Start attack” button in the top right corner of the application. You’ll get a warning that your requests may be throttled because you are using the free version. Just click OK, and the attack will start. You’ll see a popup window, and one by one your XSS attacks will be attempted.
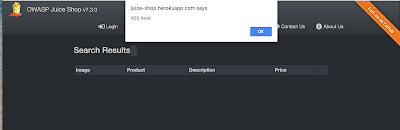
Once the attacks are finished, we can look at the attack results. There are six requests in the popup window. The first request, request 0, is simply a repeat of our original request. Requests 1-5 are the requests that we added into the Payload Options window. We can see that requests 1, 2, and 5 returned a code 200, while requests 3 and 4 returned a 500. This means that requests 1, 2, and 5 were most likely successful! You can try them yourself by pasting them into the search field of the Juice Shop page.
A few notes:
- It’s also possible, and more common, to use Burp Suite to intercept web browser requests directly, rather than going through Postman. I chose to use Postman here because it’s so easy to set up the proxy.
- If you have set up Burp Suite to intercept browser requests directly, you may be able to replay your XSS attack responses directly in the browser to see them in action.
- Another feature of the paid version of Burp Suite is the Scanner tool, which will scan for a number of vulnerabilities, including XSS.
I hope that this blog post and the two previous ones have helped you to have a greater understanding of what Cross-Site Scripting is, why it’s dangerous, and how to test for it. Next week, we’ll take a look at SQL Injection!
This comment has been removed by a blog administrator.