SQL Injection is another type of security attack that can do serious damage to your application. It’s important to find SQL Injection vulnerabilities before a malicious user does.
In SQL Injection, a malicious user sends in a SQL query through a form field which interacts with the database in an unexpected way. Here are four different things that a malicious user might do with SQL Injection:
- drop a table
- change the records of another user
- return records that the user shouldn’t have access to
- log in without appropriate credentials
- making it think that the entry has terminated, by passing in testerguy’
- adding an additional clause, such as OR 1=1
- adding a terminating statement such as ; to make sure no other SQL statement will be run
And what the database will execute is:
SELECT * from users where username = ‘testerguy’ OR 1=1;‘
Take a moment to think about the 1=1 clause. 1=1 is always true, so the database interprets this as selecting everything in the table! So this select statement is asking for all values for all the users in the table.
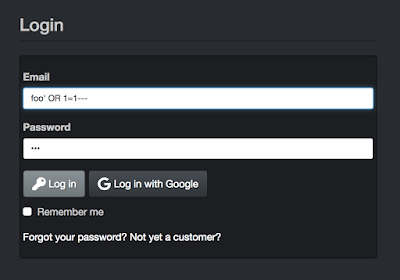
Let’s see some SQL Injection in action, using the OWASP Juice Shop. Click the login button in the top left corner of the page. We are going to use SQL injection to log in without valid credentials.
We’ll make the assumption that when the login request happens, a request like this goes to the database:
SELECT * from users where username = ‘testerguy’ AND password = ‘mysecretpass’
If the request returns results, then it’s assumed that the user is valid, and the user is logged in.
What we will want to do is try to terminate the statement so that all usernames will be returned, and so that the password isn’t looked at at all.
So we will send in:
- any username at all, such as foo
- a single quote ‘ to make it look like our entry has terminated
- the clause OR 1=1 to make the database return every username in the table
- a terminating string of — to make the database ignore everything after our request
Good information.Simple and easy to understand,well written. Enjoyed reading it.
I'm glad you enjoyed this!
Great Job done your content is very help full.I have got more information through your blogUltrasound guided injection is good. blog like these are very helpful for us. It is always good to read and upgrade ourselves.
Regards
Ultrasound guided injection